-
 Continue reading →: Code The Classics Volume 1 Review (Python)
Continue reading →: Code The Classics Volume 1 Review (Python)If you grew up in the early 90’s you may remember computing magazines that came with game programming code typed up inside, so that you the reader could type it into your computer and play the game. I’ll admit this was always a bit “hit and miss” when I attempted…
-
 Continue reading →: RSA Public-Key Cryptography (Python)
Continue reading →: RSA Public-Key Cryptography (Python)I am currently undertaking the “Encryption & Cryptography” course on FutureLearn (https://www.futurelearn.com/courses/encryption-and-cryptography/) and looking at public-key cryptography, specifically today the RSA public-key method. RSA is named after Ron Rivest, Adi Shamir and Leonard Adleman (Rivest-Shamir-Adleman; RSA) and the details for the algorithm were first published in 1977. English mathematician, Clifford…
-
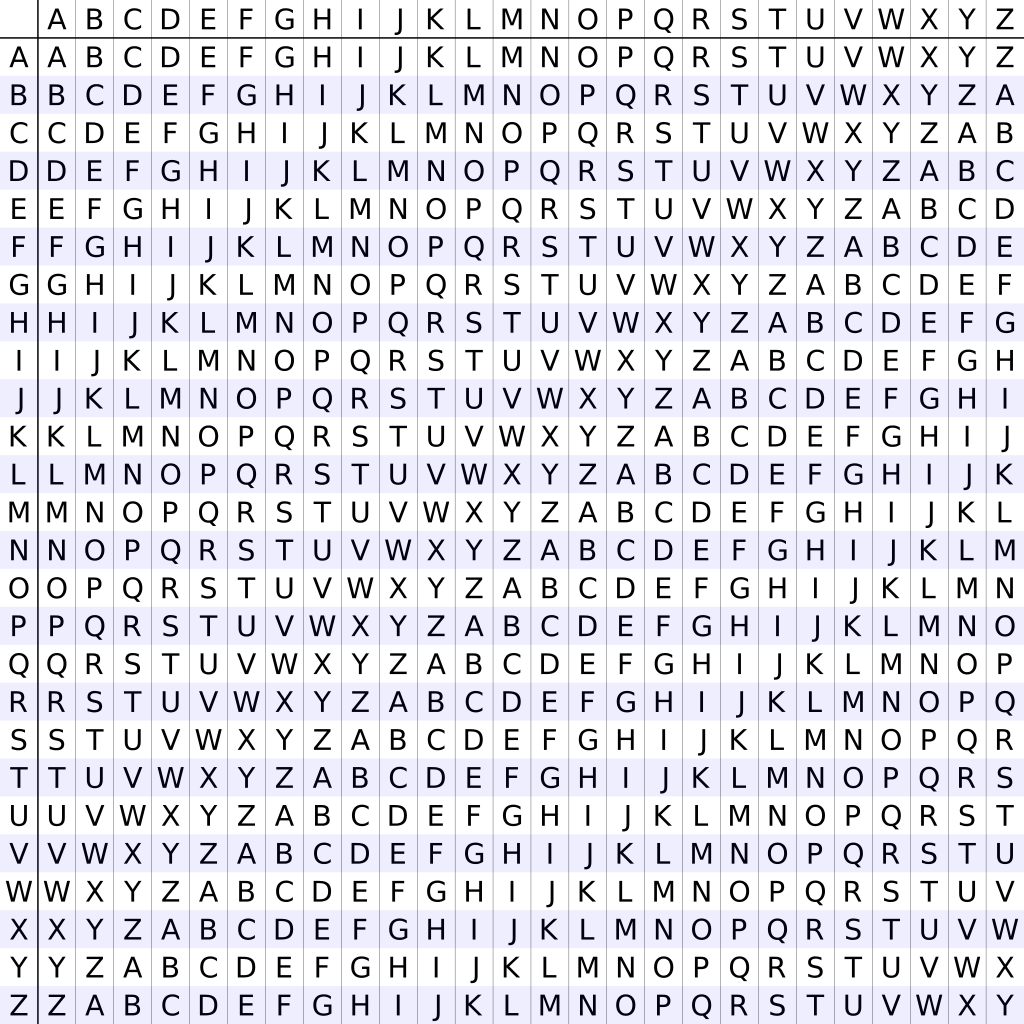 Continue reading →: Vigenère Cipher
Continue reading →: Vigenère CipherNamed after French diplomat, Blaise de Vigenère, the Vigenère cipher built on the work / ideas of Giovan Battista Bellaso. Previously I have looked at the Caesar cipher and included a Python program that can brute force crack the cipher. The Caesar cipher can be easily broken either via frequency…
-
 Continue reading →: Brute Force Caesar Cipher (Python)
Continue reading →: Brute Force Caesar Cipher (Python)“The Caesar Cipher (Caesar Shift, Caesar’s Code) is a simple, easy to implement substitution cipher. The cipher is named after Julius Caesar. The cipher works by taking the letters of the message and then shifts the letter a defined space along the alphabet. For example a shift of 1 character…
-
 Continue reading →: Nessus Essentials – Vulnerability Assessment: Installing Nessus
Continue reading →: Nessus Essentials – Vulnerability Assessment: Installing NessusVulnerability assessment tools are used to identify risks/threats that may cause security issues in a system. Today I am going to look at a vulnerability assessment tool from Tenable called Nessus Essentials, which can (manually or automatically) scan networks for vulnerabilities and then output reports. Nessus Essentials Nessus (https://www.tenable.com/products/nessus) offers…
-
 Continue reading →: Amazon Alexa Commands
Continue reading →: Amazon Alexa CommandsWith the November Black Friday and Cyber Monday deals flying about some readers may be tempted to pick up an Amazon Alexa. So today I thought I would post a brief article on some of the easter egg type voice commands that you may like, after all Alexa can do…
-
 Continue reading →: Go Go Functions! The Basics Of Functions (Go)
Continue reading →: Go Go Functions! The Basics Of Functions (Go)So far I’ve introduced Go with a “Hello World” and looked at the basics of variables. With today’s blog post I hope to take a look at the basics of functions within Go. I am going to give examples of a few functions that I have learned and then in…
-
 Continue reading →: Variable Basics (Go)
Continue reading →: Variable Basics (Go)Variables and programming languages go hand in hand, and Go is no different. In Go variables can be defined using the keyword var, the variable name and the variable type for example: var name_of_player string var player_score int Or multiple variables can be defined using var () for example: var (…
-
 Continue reading →: An Introduction to Go with “Hello World”(Go)
Continue reading →: An Introduction to Go with “Hello World”(Go)This week I started looking at Go and as I am new to Go, decided that a few blog entires was needed to help me learn and remember details. History Go, also known as Golang, is a programming language that started as an idea in 2007 and saw its first…
-
 Continue reading →: Virtual Box – Scripting and Network Options (Mac OS X / Linux)
Continue reading →: Virtual Box – Scripting and Network Options (Mac OS X / Linux)As well as allowing for the creation of virtual computers, Virtual Box also gives several settings for virtual networks. Following on from my last blog post (here) I am now going to take a brief look at the Virtual Box network settings. Virtual Box Network Settings Virtual network settings can…
Hello,
Welcome to GeekTechStuff
my home away from home and where I will be sharing my adventures in the world of technology and all things geek.
The technology subjects have varied over the years from Python code to handle ciphers and Pig Latin, to IoT sensors in Azure and Python handling Bluetooth, to Ansible and Terraform and material around DevOps.
Let’s connect
Join the fun!
Stay updated with the sites latest blog posts by joining the newsletter.

You must be logged in to post a comment.